Unify all your policies across clouds and the stack with Policy Orchestration
Hexa is the open-source, standards-based Policy Orchestration software for multi-cloud and hybrid businesses.

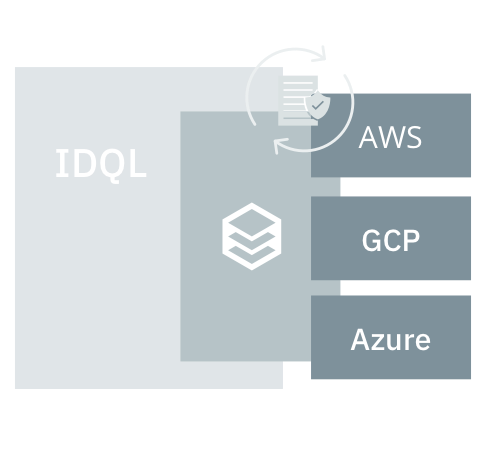
Hexa Policy Orchestration (Hexa) and Identity Query Language (IDQL) were purpose-built to solve the proliferation of Policy Orchestration problems caused by today’s hybrid cloud and multi-cloud world. Together, Hexa and IDQL enable you to manage all of your policies consistently across clouds and vendors so you can unify access policy management.
Hexa’s three steps to success
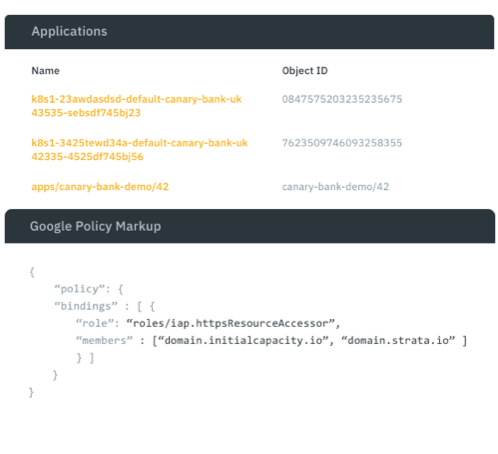
1. Policy and resource discovery
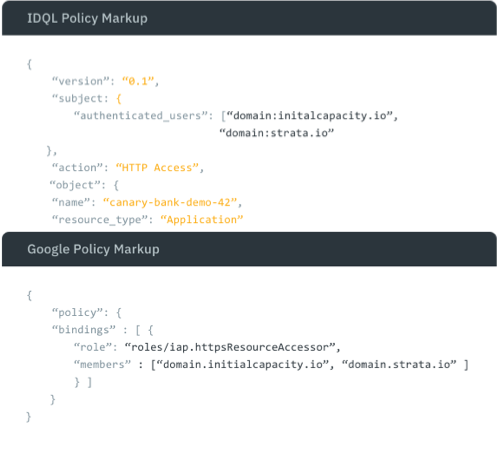
2. Translate IDQL into native policy
3. Orchestrate policy across clouds and the stack
Benefits of Policy Orchestration with Hexa and IDQL
Open source vendor-agnostic Policy Orchestration software that makes any cloud work together.

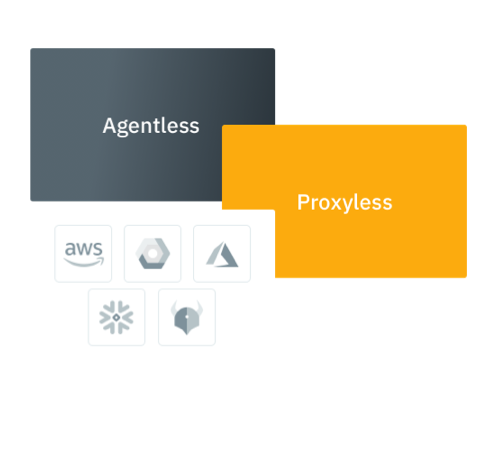
Agentless and proxyless Policy Orchestration
Implement in hours without changes to your existing infrastructure.
Built with a multi-cloud-native architecture, Fabric Policy Orchestration has an agentless and proxyless architecture enabling speed and agility.

Universal access policy
Manage access policy that works across disparate systems to help enable a Zero Trust architecture.
Authentication and authorization is orchestrated universally and consistently across apps, platforms, infrastructure, data, and networks.

Declarative policy
Understand who has access to which apps and data at a glance.
Leveraging the simple, human-readable policy format of IDQL, Hexa can be implemented quickly.

Distributed policy management
Orchestrate access policy securely through APIs with no change required to target systems.
Hexa uses IDQL policy to work across multiple identity systems and multi-cloud use cases.

Policy-as-code
Bring identity policy into code for large-scale automation.
Hexa works seamlessly with your CI/CD and DevOps tools to manage access to your apps as part of the SDLC. You can version, rollback, automate, script, and scale using config management.

Break lock-in
Break lock-in and enjoy portability and vendor choice.
Hexa’s policy abstraction layer allows you to move from cloud-to-cloud so you can enjoy best-of-breed solutions.
Join the community
Behind the scenes of Policy Orchestration
Hexa in the wild
Hexa (the software) + IDQL (the standard) make multi-cloud work
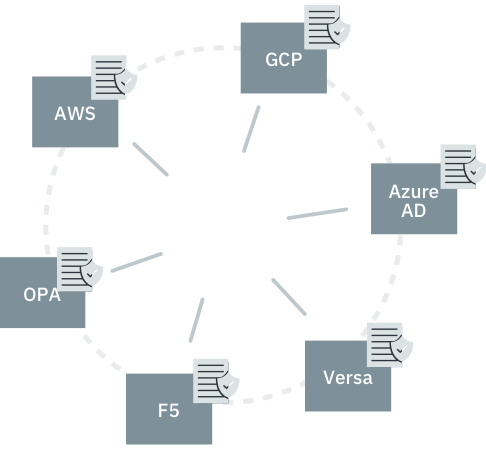
The Hexa Policy Orchestration Gateway takes IDQL policy and distributes it across your clouds and translates it into the native, imperative access control policies inside the systems you use today. You then have a policy abstraction layer across your clouds, apps, data, and networks. Together, Hexa and IDQL provide simple management of access policy for:
-
Web apps that work across cloud identity systems from Okta and Azure AD
-
Cloud data on Snowflake, Databricks, AWS, GCP, and other cloud storage
Policy discovery
-
Analyze your Identity Fabric and inventory key apps, data, and policies
-
What apps exist? Where are they?
-
What policies, users, and roles exist?
Policy translation
-
During policy discovery, translate native, imperative policies into IDQL
-
During policy orchestration, translate IDQL into native, imperative policies of the target system(s)
Policy orchestration
-
Distribute policies to be enforced by IDPs, clouds, IaaS, and network systems
-
Cloud-based architecture does not require proxy or local code
-
Extensible, open source model to build your own integration
We’re building open source Policy Orchestration software to change and simplify the way access is managed across IT. Join us.
Features of Hexa Policy Orchestration
Manage the policies that govern access across multiple clouds.
Open source
The Hexa Policy Orchestration Gateway is submitted as a CNCF sandbox project.
East <-> West policy
Policy is unified across AWS, Azure, and GCP (and any other cloud platform).
North <-> South policy
Policy is also managed across the stack for apps, data, platform, and networking.
Zero overhead
Policy orchestration is done through admin processes, not run time.
Enterprise-ready
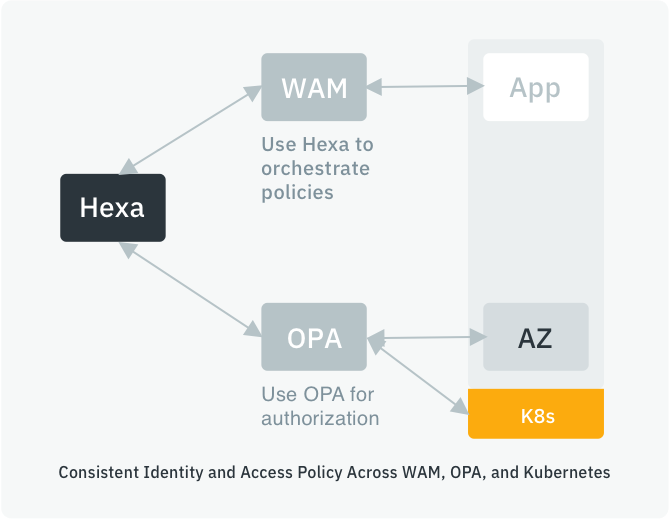
Hexa works with your containers, Kubernetes, OPA, and CI/CD tools and processes.
Simple security
IDQL is a clear, declarative policy that is simple to understand and enforce.
Simplified compliance
Easy-to-read access and user reports generated from across your clouds.
Seamless API integration
Native integration with cloud and identity APIs insulates you from changing cloud APIs
Natively integrated with other CNCF tools (coming soon…)
Orchestrate OPA policies with your other access management systems. Orchestrate K8S policies and run Hexa on Kubernetes.
Orchestrate access policies across clouds and up and down the stack
App, platform, data, and network systems orchestrated independently of target systems.
FAQ
What is Hexa?
Hexa takes IDQL policy, distributes it across your clouds, and translates it into the native, imperative, access control policies within target systems. With Hexa, you create a policy abstraction layer across clouds, apps, data, and networks.
What is IDQL?
Identity Query Language (IDQL) is a declarative access policy and set of APIs that enables the mapping of a centrally managed policy into the native format of multiple clouds and application platforms.
How is Hexa different from OPA?
Hexa’s IDQL is a new standard created for universal access Policy Orchestration and governance. They are complementary because OPA’s Rego and IDQL do different things. IDQL is for Policy Orchestration, giving you control across distributed cloud systems (including OPA policies), using a simple declarative policy. OPA policies are focused on authorizing a specific transaction and Kubernetes.
- Pair Hexa with Open Policy Agent (OPA) to orchestrate enterprise policies to be enforced by OPA. Make OPA policy visible with Hexa discovery.
Why use IDQL and Hexa Policy Orchestration?
Hexa allows you to translate and orchestrate IDQL. IDQL is a declarative policy that is easy to understand and apply across your tech stack. It gives you better, more consistent control over apps, data, and network access.
Why does the industry need a new standard?
While other standards like SAML and OpenID Connect focus on single sign-on and federation, access policy has not been standardized across applications and cloud platforms. Without IDQL, identity and access fragmentation will continue to be a huge challenge for enterprises that implement a multi- and hybrid cloud infrastructure.
What standards group manages Hexa/IDQL?
Hexa has been submitted to the Cloud Native Computing Foundation (CNCF). The CNCF is the vendor-neutral organization that will manage the ongoing development of Hexa/IDQL.
How does IDQL compare to existing standards?
Other standards focus on different aspects of the identity landscape, such as:
- Open Policy Agent (OPA) focuses on Kubernetes cluster management, networking, microservices, and APIs rather than end-user identity. In addition, OPA’s policy language, Rego, is not an industry standard.
- SPIFFE/Spire deals with app-to-app identity using x.509, not end-user identity
- SAML, OpenID Connect, and OAuth are all protocols for authentication but not end-user identity policy.
- XACML focuses on fine-grained authorization, not end-user identity policy. While declarative, it is too complex for cloud native use cases.